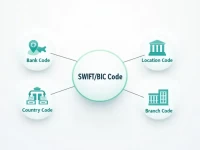
SWIFT BIC Codes Vital for International Money Transfers
This article provides an in-depth analysis of the structure of SWIFT/BIC codes and their significance in international remittances. It offers practical advice for correctly using these codes to ensure a smooth and error-free remittance process.